where P(yj |xi) is the fraction of examples with X = xi that belong to class yj . The entropy after splitting on X is given by the weighted entropy of the children nodes:
What will be an ideal response?
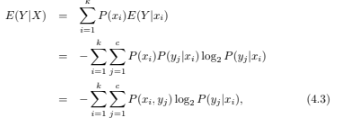
Computer Science & Information Technology
You might also like to view...
What type of error occurs when a valid subject using a biometric authenticator is not authenticated?
A. A Type 1 error B. A Type 2 error C. A Type 3 error D. A Type 4 error
Computer Science & Information Technology
Declaring instance variables ________ is known as data hiding or information hiding.
a. secure b. private c. static d. masked
Computer Science & Information Technology