Let set U = {0, 1, 2, 3, 4, 5, 6, 7, 8, 9}, A = {0, 1, 2, 3}, B = {1, 3, 5, 7, 9}, and C = {x | x 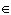 N such that 3
N such that 3 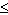 x
x 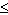 15}. Perform the following operation.A
15}. Perform the following operation.A 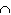 (B
(B ![]()
src="https://qoschin.com/media/4/ppg__examview__ch32__00001_res__sa019-5.jpg" border="0"> C)
What will be an ideal response?
{3}
Computer Science & Information Technology
You might also like to view...
Which of the following is an example of willful damage?
A. Cybercrime B. User operator error C. Hazardous chemical exposure D. Public health emergency
Computer Science & Information Technology
Mary is a security risk analyst for an insurance company. She is currently examining a scenario where a hacker might use a SQL injection attack to deface a web server due to a missing patch in the company's web application. In this scenario, what is the risk?
A. Unpatched web application B. Web defacement C. Hacker D. Operating system
Computer Science & Information Technology