Establishing security policy, objectives, processes and procedures is part of the ______ step.
A. plan B. check
C. act D. none of the
A. plan
Computer Science & Information Technology
You might also like to view...
If a password is salted with a 24-bit random number, how big is the dictionary attack search space for a 200,000 word dictionary?
What will be an ideal response?
Computer Science & Information Technology
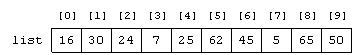 In a sequential search, how many key comparisons would have to be made on the list in the accompanying figure to find the number 5?
In a sequential search, how many key comparisons would have to be made on the list in the accompanying figure to find the number 5?
A. 4 B. 5 C. 7 D. 8
Computer Science & Information Technology