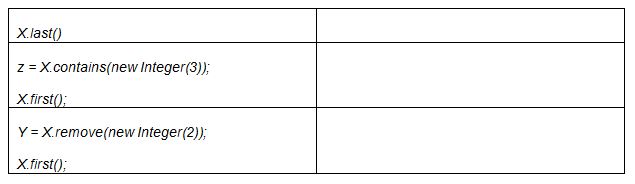
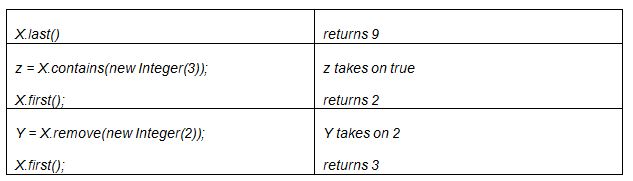
Given the resulting list X, what would be the result of each of the following?
Computer Science & Information Technology
You might also like to view...
There are several advantages to ________, one of which is the fact that a physically distributed workforce is less of a target for terrorist attacks
Fill in the blank(s) with correct word
Computer Science & Information Technology
Unsolicited bulk e-mail is referred to as __________.
A. spam B. propagating C. phishing D. crimeware
Computer Science & Information Technology