Modifying the system’s TCP/IP network code to selectively drop an entry for an incomplete connection from the TCP connections table when it overflows, allowing a new connection attempt to proceed is _______.
A. poison packet B. slashdot
C. backscatter traffic D. random drop
D. random drop
Computer Science & Information Technology
You might also like to view...
What is the following kind of statement called?
int counter;
Computer Science & Information Technology
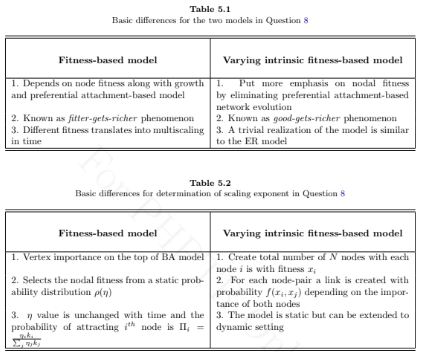
What are the basic differences between the fitness-based model [ 3] and the varying intrinsic fitness-based model [ 4]? Distinguish these two models in the light of analytical determination of scaling exponents. Compare the above evolution models with the preferential attachment– based model.
Computer Science & Information Technology