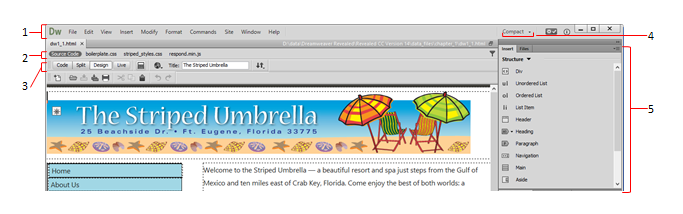
Item ____ in the figure above is the Workspace switcher.
A. 2
B. 3
C. 4
D. 5
Answer: C
Computer Science & Information Technology
You might also like to view...
Which of the following methods should be used when classified or sensitive data is stored on a server?
A. Directory encryption B. Whole disk encryption C. File encryption D. Partition encryption
Computer Science & Information Technology
A self-contained program that spreads through a computer network by exploiting security holes is called a
a. hack. b. rogue. c. Trojan horse. d. virus. e. worm.
Computer Science & Information Technology