Briefly describe IP spoofing attacks.
What will be an ideal response?
IP spoofing is a technique attackers use in which they send packets to the victim or target computer with a false source address. The victim is unaware that the packet is not from a trusted host, and so it accepts the packet and sends a response "back" to the indicated source computer.?Since the attacker sending the spoofed packet cannot see the response, he must guess the proper sequence numbers to send the final ACK packet as if it had come from the "real" source. If this attempt is successful, the hacker may have a connection to the victim's machine and be able to hold it for as long as the computer remains active. There are two methods for resolving these problems: sequence guessing and source routing.
You might also like to view...
Match the following terms with their description
I. OOP II. VBA III. Object collection IV. Object model V. Object A. Powerful programming language B. The active chart or chart contained in a ChartObject C. Can also serve as containers for other objects D. Uses a hierarchy of classes E. Consists of a hierarchical collection of objects
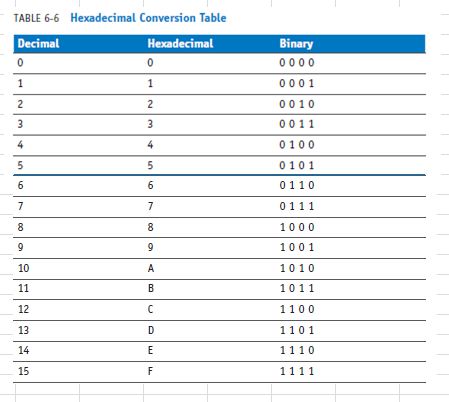
What is the equivalent hexadecimal number for 13? Refer to Table 6-6