List the types of local resource that are vulnerable to an attack by an untrusted program that is downloaded from a remote site and run in a local computer.
What will be an ideal response?
Objects in the file system e.g. files, directories can be read/written/created/deleted using the rights of the local user who runs the program.
Network communication - the program might attempt to create sockets, connect to them, send messages etc. Access to printers.
It may also impersonate the user in various ways, for example, sending/receiving email
Computer Science & Information Technology
You might also like to view...
The organization of the file system on a server has no impact on network performance or security.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
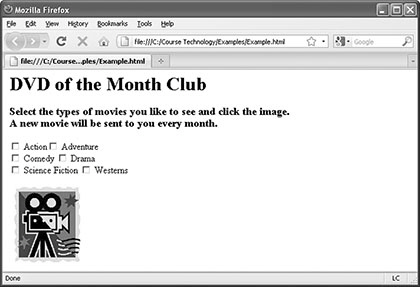 A(n) ____ button is seen in the accompanying figure.
A(n) ____ button is seen in the accompanying figure.
A. image submit B. push C. submit D. reset
Computer Science & Information Technology