Describe shared key authentication.
What will be an ideal response?
With shared key authentication, both the AP and the station are given the same key value in advance. (In other words, they "share" the key value.) The station first sends an authentication frame to the AP, and the AP responds with an authentication frame that contains a block of text known as the challenge text. The station must encrypt the text with its key value and return it to the AP in an authentication frame. The AP will then decrypt what was returned with its own key to see if it matches the original challenge text. If it does, the AP sends an authentication frame signifying the result of the authentication.
You might also like to view...
Consider the transactions shown in Table 7.14, with an item taxonomy given in Figure 7.25.
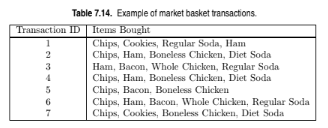
(a) What are the main challenges of mining association rules with item
taxonomy?
(b) Consider the approach where each transaction t is replaced by an ex-
tended transaction t'
that contains all the items in t as well as their re-
spective ancestors. For example, the transaction t = { Chips, Cookies}
will be replaced by t'
= {Chips, Cookies, Snack Food, Food}. Use this
approach to derive all frequent itemsets (up to size 4) with support ?
70%.
(c) Consider an alternative approach where the frequent itemsets are gen-
erated one level at a time. Initially, all the frequent itemsets involving
items at the highest level of the hierarchy are generated. Next, we use
the frequent itemsets discovered at the higher level of the hierarchy to
generate candidate itemsets involving items at the lower levels of the hi-
erarchy. For example, we generate the candidate itemset {Chips, Diet
Soda} only if {Snack Food, Soda} is frequent. Use this ap
Promoting is another term for uploading.
Answer the following statement true (T) or false (F)