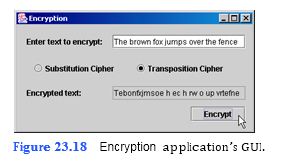
Write an application that encrypts a message from the user (Fig. 23.18). The application should be able to encrypt the message in two different ways: substitution cipher and transposition cipher (both described below). The user should be able to enter the message in a JTextField and select the desired method of encryption. The encrypted message is then displayed in an uneditable JTextField. In a substitution cipher, every character in the English alphabet is represented by a dif- ferent character in a substitution String, which we will refer to as the substitution alphabet. Every time a letter occurs in the English sentence, it is replaced by the letter in the corre- sponding index of the substitution String. As an example of a substitution cipher, let’s e
a) Copying the template to your working directory. Copy the C:Examples Tutorial23ExercisesCipherEncryption directory to your C:SimplyJava directory.
b) Opening the template file. Open the Encryption.java file in your text editor.
c) Adding code to the substitutionCipher method. In the substitutionCipher method (lines 126–140), English and substitution alphabet Strings have been declared for you as normalAlphabet and cipherAlphabet, respectively. Other Strings that you will be using have already been defined for you—cipher is an empty String you will use to store the encrypted text and plain contains the text entered by the user. After the declaration of the Strings, add an empty for state- ment that loops for each character in plain.
d) Performing the substitution encryption. Inside the for statement you added in Step c, create an int variable index and assign to it the index in normalAlphabet where the current character in plain
```
1 // Encryption.java
2 // Encrypts data entered by users.
3 import java.awt.*;
4 import java.awt.event.*;
5 import java.text.*;
6 import javax.swing.*;
7
8 public class Encryption extends JFrame
9 {
10 // JLabel and JTextField for user input
11 private JLabel instructionJLabel;
12 private JTextField plainJTextField;
13
14 // ButtonGroup to contain JRadioButtons
15 private ButtonGroup radioButtonGroup;
16
17 // JRadioButtons to allow two types of encryption
18 private JRadioButton substitutionJRadioButton;
19 private JRadioButton transpositionJRadioButton;
20
21 // JLabel and JTextField for output
22 private JLabel resultJLabel;
23 private JTextField cipherJTextField;
24
25 // JButton to encrypt phrase
26 private JButton encryptJButton;
27
28 // no-argument constructor
29 public Encryption()
30 {
31 createUserInterface();
32 }
33
34 // create and position GUI components; register event handlers
35 private void createUserInterface()
36 {
37 // get content pane for attaching GUI components
38 Container contentPane = getContentPane();
39
40 // enable explicit positioning of GUI components
41 contentPane.setLayout( null );
42
43 // set up instructionJLabel
44 instructionJLabel = new JLabel();
45 instructionJLabel.setBounds( 16, 16, 126, 21 );
46 instructionJLabel.setText( "Enter text to encrypt:" );
47 contentPane.add( instructionJLabel );
48
49 // set up plainJTextField
50 plainJTextField = new JTextField();
51 plainJTextField.setBounds( 150, 16, 207, 21 );
52 contentPane.add( plainJTextField );
53
54 // create logical relationship between JRadioButtons
55 radioButtonGroup = new ButtonGroup();
56
57 // set up substitutionJRadioButton
58 substitutionJRadioButton = new JRadioButton();
59 substitutionJRadioButton.setBounds( 24, 56, 140, 24 );
60 substitutionJRadioButton.setText( "Substitution Cipher" );
61 substitutionJRadioButton.setSelected( true );
62 radioButtonGroup.add( substitutionJRadioButton );
63 contentPane.add( substitutionJRadioButton );
64
65 // set up transpositionJRadioButton
66 transpositionJRadioButton = new JRadioButton();
67 transpositionJRadioButton.setBounds( 184, 56, 148, 24 );
68 transpositionJRadioButton.setText( "Transposition Cipher" );
69 radioButtonGroup.add( transpositionJRadioButton );
70 contentPane.add( transpositionJRadioButton );
71
72 // set up resultJLabel
73 resultJLabel = new JLabel();
74 resultJLabel.setBounds( 16, 96, 100, 21 );
75 resultJLabel.setText( "Encrypted text:" );
76 contentPane.add( resultJLabel );
77
78 // set up cipherJTextField
79 cipherJTextField = new JTextField();
80 cipherJTextField.setBounds( 150, 96, 207, 21 );
81 cipherJTextField.setEditable( false );
82 contentPane.add( cipherJTextField );
83
84 // set up encryptJButton
85 encryptJButton = new JButton();
86 encryptJButton.setBounds( 272, 128, 85, 23 );
87 encryptJButton.setText( "Encrypt" );
88 contentPane.add( encryptJButton );
89 encryptJButton.addActionListener(
90
91 new ActionListener() // anonymous inner class
92 {
93 // event handler called when encryptJButton is pressed
94 public void actionPerformed( ActionEvent event )
95 {
96 encryptJButtonActionPerformed( event );
97 }
98
99 } // end anonymous inner class
100
101 ); // end call to addActionListener
102
103 // set properties of application’s window
104 setTitle( "Encryption" ); // set title bar string
105 setSize( 376, 192 ); // set window size
106 setVisible( true ); // display window
107
108 } // end method createUserInterface
109
110 // encrypt a String of characters
111 private void encryptJButtonActionPerformed( ActionEvent event )
112 {
113 // determine the selected JRadioButton
114 if ( substitutionJRadioButton.isSelected() )
115 {
116 substitutionCipher(); // call substitutionCipher
117 }
118 else
119 {
120 transpositionCipher(); // call transpositionCipher
121 }
122
123 } // end method encryptJButtonActionPerformed
124
125 // using the substitution cipher, display encrypted text
126 private void substitutionCipher()
127 {
128 // normal alphabet String
129 String normalAlphabet = "abcdefghijklmnopqrstuvwxyz .!?,";
130
131 // substitution alphabet String
132 String cipherAlphabet = "cdefg.hijk!lmn opqr?stuv,wxyzab";
133
134 String cipher = ""; // encrypted String
135
136 // get
137 String
138 String
139
140 // iterate through the length of the plainText String
141 for ( int i = 0; i < plain.length(); i++ )
142 {
143 // get the normal alphabet index of the current letter
144 int index = normalAlphabet.indexOf( plain.charAt( i ) );
145
146 // valid index
147 if ( index != -1 )
136 // get
137 String
138 String
139
140 // iterate through the length of the plainText String
141 for ( int i = 0; i < plain.length(); i++ )
142 {
143 // get the normal alphabet index of the current letter
144 int index = normalAlphabet.indexOf( plain.charAt( i ) );
145
146 // valid index
147 if ( index != -1 )
148 {
149 // add the cipher alphabet letter of that index to cipher
150 cipher += cipherAlphabet.charAt( index );
151 }
152
153 } // end for
154
155 // output the encrypted String
156 cipherJTextField.setText( cipher );
157
158 } // end method substitutionCipher
159
160 // using
161 private void transpositionCipher()
162 {
163 String firstWord = ""; // first word
164 String lastWord = ""; // second word
165
166 // get
167 String text from plainJTextField
plainText = plainJTextField.getText();
168
169 // create first and second words
170 for ( int counter = 0; counter < plainText.length();
171 counter++ )
172 {
173 if ( ( counter % 2 ) == 0 )
174 {
175 // add character from specified location to firstWord
176 firstWord += plainText.charAt( counter );
177 }
178 else
179 {
180 // add character from specified location to lastWord
181 lastWord += plainText.charAt( counter );
182 }
183
184 } // loop through the entire String
185
186 // output encrypted text
187 cipherJTextField.setText( firstWord + " " + lastWord );
188
189 } // end method transpositionCipher
190
191 // main method
192 public static void main( String[] args )
193 {
194 Encryption application = new Encryption();
195 application.setDefaultCloseOperation( JFrame.EXIT_ON_CLOSE );
196
197 } // end method main
198
199 } // end class Encryption
```
You might also like to view...
A technician recently set up a new wired network and wants to ensure only his computers can use it. Which of the following is the most secure way to accomplish this?
a. Disable the extra ports on the router b. Enable an intrusion detection system c. Make sure the computers are using strong passwords d. Assign static IP addresses to the computers
Screen resolution indicates the number of ____ that the computer uses to display the letters, numbers, graphics, and background you see on the screen.
A. picas B. characters C. pixels D. points