A ________ is a type of malware that is attached to a host file and has the ability to replicate, or copy, itself.
A. worm
B. zombie
C. Trojan horse
D. virus
Answer: D
Computer Science & Information Technology
You might also like to view...
When you set the width of a horizontal rule as a percentage of the page rather than in ____________________, it resizes itself proportionately when viewed on different-sized monitors and resolutions.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
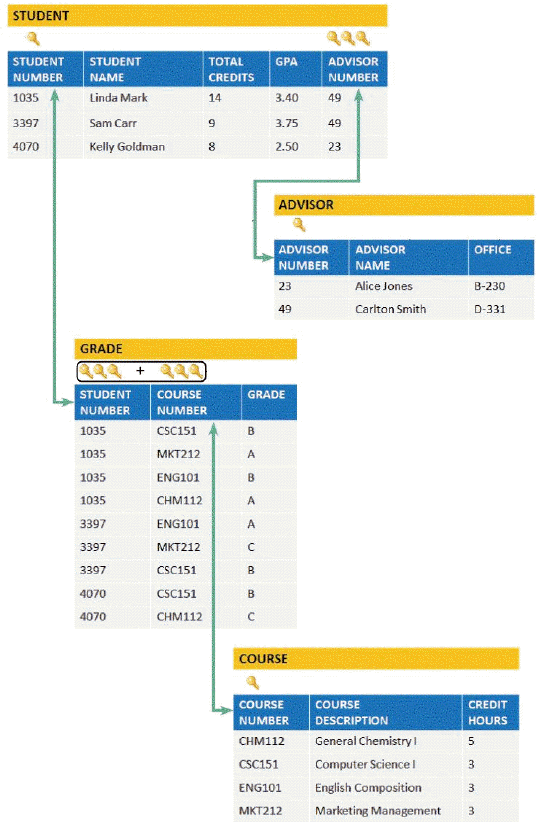
A. ?candidate key B. ?secondary key C. ?combination key D. ?foreign key
Computer Science & Information Technology