List three types of security policy.
What will be an ideal response?
Acceptable use policy
Password policy
Wireless policy
Computer Science & Information Technology
You might also like to view...
Subtotaled rows that are totaled and summarized are referred to as ________ data
A) summary B) detail C) actual D) subtotal
Computer Science & Information Technology
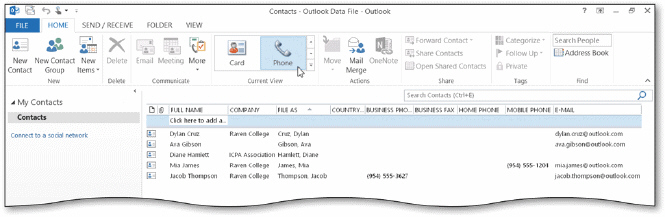 If the Phone button is not displayed in the Current View group as shown in the accompanying figure, tap or click the ____ button.
If the Phone button is not displayed in the Current View group as shown in the accompanying figure, tap or click the ____ button.
A. Additional Views B. Options C. New Views D. More
Computer Science & Information Technology