Using the Help feature, determine what security features are available in Visible Analyst®, or another CASE tool. Describe what you found in a brief memo, and include screen shots if possible.
What will be an ideal response?
Visible Analyst describes different security environments for single-user vs. network versions. Here are several screens that explain single-user security:
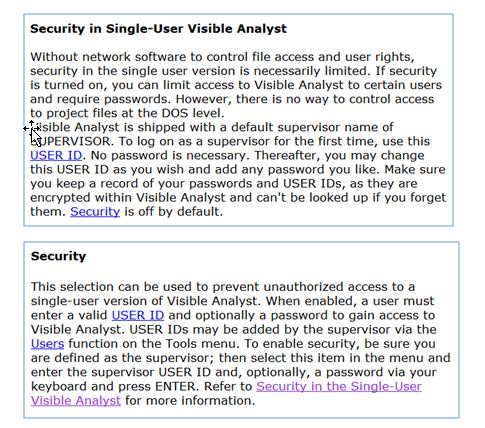
Here is how to turn on the Security feature,
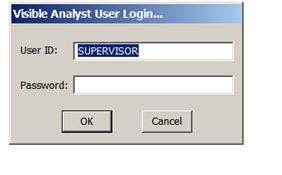
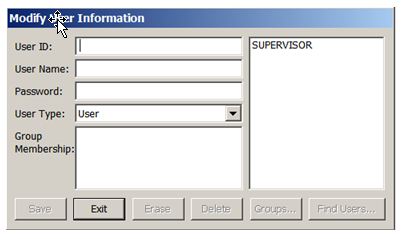
And here is where the Supervisor can add authorized users and groups:
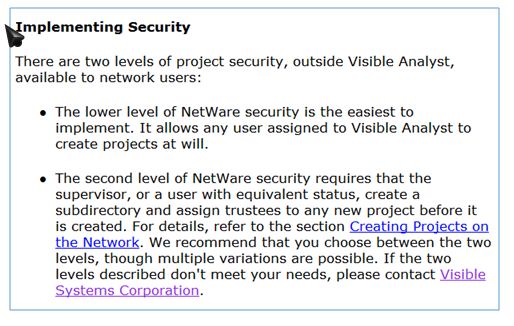
Here is a brief discussion of the network version, which includes typical network security features and methods.
You might also like to view...
In the RGB system, each color can have a value from 0 to ________
Fill in the blank(s) with correct word
Answer the following statements true (T) or false (F)
1. When configuring remote installations for wireless networks, the receive site needs to be able to see the multipoint distribution antenna site. 2. If the signal quality drops from excellent to good, the antenna or access point should be replaced. 3. The term enterprise network is used to describe the network used by a large company. 4. The four layers of the TCP/IP model are application, network,Internet, and data link. 5. Converting 65 to its binary equivalent yields 1 0 0 0 0 0 1.