When an IPsec communication begins between two computers, the computers first exchange ____ to authenticate the receiver and sender.
A. keys
B. certificates
C. passwords
D. tickets
Answer: B
Computer Science & Information Technology
You might also like to view...
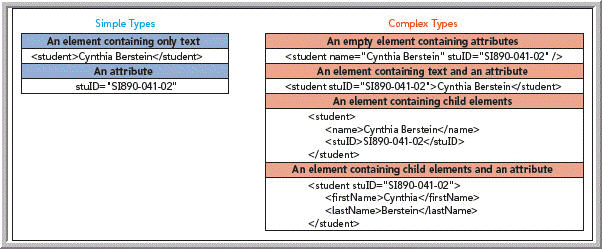 As shown in the accompanying figure, XML Schema supports ____ types of content.
As shown in the accompanying figure, XML Schema supports ____ types of content.
A. two B. three C. four D. six
Computer Science & Information Technology
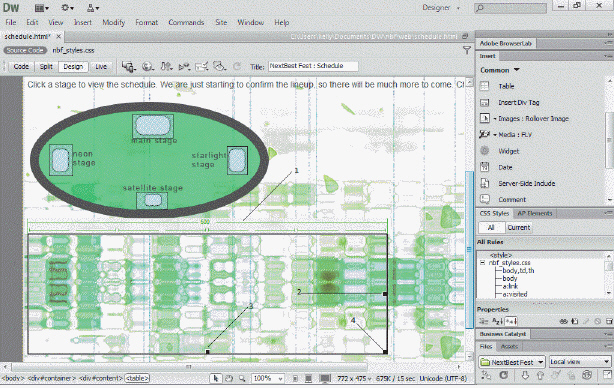 When you create a table like the one in the accompanying figure, Dreamweaver inserts a(n) ____ in each cell.
When you create a table like the one in the accompanying figure, Dreamweaver inserts a(n) ____ in each cell.
A. break tag B. nonbreaking space C. hyperlink D. anchor tag
Computer Science & Information Technology