________ attacks are those that involve malware, computer or network intrusion, or other cyberattacks on critical computer systems
Fill in the blank(s) with the appropriate word(s).
Answer: Computer network
Computer Science & Information Technology
You might also like to view...
How would you explain scalability? How would you ensure that scalability has been considered in Zevo’s requirements model?
What will be an ideal response?
Computer Science & Information Technology
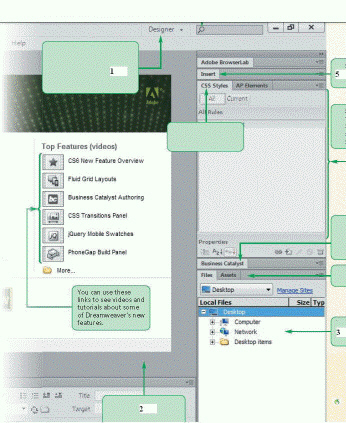 In the accompanying figure, the item marked ____ is the workplace switcher.
In the accompanying figure, the item marked ____ is the workplace switcher.
A. 1 B. 2 C. 4 D. 5
Computer Science & Information Technology