Data-flow diagrams trace all data in an information system from the point at which data enter the system to their final resting places
Indicate whether the statement is true or false
TRUE
Computer Science & Information Technology
You might also like to view...
All Cisco PIX series firewalls offer AES, DES, and 3DES built-in encryption
Indicate whether the statement is true or false.
Computer Science & Information Technology
What is the output of the following program?
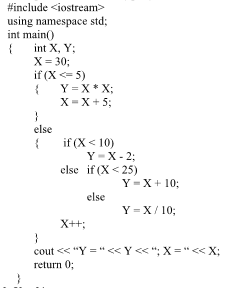
A. Y = 3, X = 31
B. Y = 28, X =31
C. Y = 40, X = 31
D. Y = 900, X = 35
E. None of the above are correct
Computer Science & Information Technology