The system will enter an unsafe state if ________.
Consider the following system state:
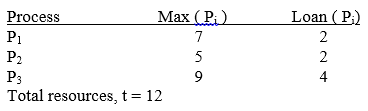
a) process P1 is allocated one additional resource
b) process P2 is allocated two additional resources
c) process P3 is allocated three additional resources
d) process P2 is allocated one additional resource
c) process P3 is allocated three additional resources
Computer Science & Information Technology
You might also like to view...
Which of the following is NOT a common file name extension?
a. .docx b. .jpg c. .pptx d. .zipped
Computer Science & Information Technology
You are replaceing your old 802.11b wireless router with a new 802.1g wireless router. You have just changed the SSID, you enabled WPA2, and finally, you set a passphrase for the level of encryption chosen. What should you do NEXT?
a. Update your firmware b. Change the admin password c. Enable AES on the router d. Configure WEP
Computer Science & Information Technology