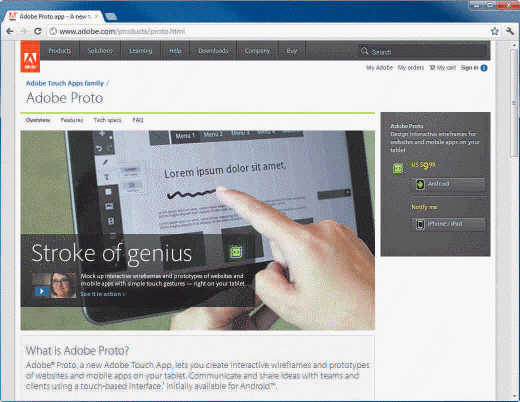
 The application in the accompanying figure produces ____ wireframes.
The application in the accompanying figure produces ____ wireframes.
A. high-resolution
B. low-fidelity
C. high-fidelity
D. indexed
Answer: C
Computer Science & Information Technology
You might also like to view...
Realistic ________ should be assigned to each step of the plan
A) backups B) stakeholders C) software D) time limits
Computer Science & Information Technology
Privacy is only important if you have something to hide.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology