Solve the linear equation. 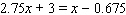
A. ![]()
B. ![]()
C. ![]()
D. ![]()
E. no solution
Answer: B
Computer Science & Information Technology
You might also like to view...
An organization needs to implement a large PKI. Network engineers are concerned that repeated transmission of the OCSP will impact network performance.Which of the following should the security analyst recommend is lieu of an OCSP?
A. CSR B. CRL C. CA D. OID
Computer Science & Information Technology
WEP's RC4 approach to encryption uses a 24-bit string of characters added to transmitted data, such that the same plain-text data frame will never appear as the same WEP-encrypted data frame. What is this string of characters called?
a. Initialization vector b. Chips c. Orthogonal descriptor d. Session key
Computer Science & Information Technology