Briefly describe each of the following as they relate to digital security and privacy:
Viruses and malwarePrivacyHealth concernsEnvironmental issues
What will be an ideal response?
?Student descriptions will vary but they should touch on the three technologies listed below:?Malware, short for malicious software, is software that typically acts without a user's knowledge and deliberately alters the computer's or mobile device's operations. Examples of malware include viruses, worms, trojan horses, rootkits, spyware, adware, and zombies. Each of these types of malware attacks your computer or mobile device differently. Some are harmless pranks that temporarily freeze, play sounds, or display messages on your computer or mobile device. Others destroy or corrupt data, instructions, and information stored on the infected computer or mobile device. Nearly every life event is stored in a computer somewhere ... in medical records, credit reports, tax records, etc. In many instances, where personal and confidential records were not protected properly, individuals have found their privacy violated and identities stolen. Some techniques you can use to protect yourself from identity theft include shredding financial documents before discarding them, never clicking links in unsolicited email messages, and enrolling in a credit monitoring service. Adults, teens, and children around the world are using online social networks to share their photos, videos, journals, music, and other personal information publicly. Some of these unsuspecting, innocent computer users have fallen victim to crimes committed by dangerous strangers. Protect yourself and your dependents from these criminals by being cautious in email messages and on websites. For example, do not share information that would allow others to identify or locate you, and do not disclose identification numbers, user names, passwords, or other personal security details. A user name is a unique combination of characters, such as letters of the alphabet or numbers, that identifies one specific user. A password is a private combination of characters associated with a user name.?Prolonged or improper computer and mobile device use can lead to injuries or disorders of the hands, wrists, elbows, eyes, neck, and back. Computer and mobile device users can protect themselves from these health risks through proper workplace design, good posture while at the computer, and appropriately spaced work breaks. With the growing use of earbuds and headphones, some users are experiencing hearing loss. Ways to protect your hearing when using these devices were presented earlier in this module. Two behavioral health risks are technology addiction and technology overload. Technology addiction occurs when someone becomes obsessed with using technology. Individuals suffering from technology overload feel distressed when deprived of computers and mobile devices. Once recognized, both technology addiction and technology overload are treatable disorders. ?Manufacturing processes for computers and mobile devices, along withe-waste(discarded computers and mobile devices), are depleting natural resources and polluting the environment. When computers and mobile devices are stored in basements or other locations, disposed of in landfills, or burned in incinerators, they can release toxic materials and potentially dangerous levels of lead, mercury, and flame retardants.Green computinginvolves reducing the electricity consumed and environmental waste generated when using a computer. Strategies that support green computing include recycling, using energy-efficient hardware and energy-saving features, regulating manufacturing processes, extending the life of computers, and immediately donating or properly disposing of replaced computers. When you purchase a new computer, some retailers offer to dispose of your old computer properly.
You might also like to view...
On switch SW3, find out spanning tree information. Who is the root?
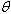
What will be an ideal response?
Employees at a small publishing company were dissatisfied with their project tracking system because it didn't allow them to record enough detail. To solve the problem, they created another system that recorded some of the same information, but allowed them to add even more detail about the schedules and budgets. As a result, the company had _____ systems.?
Fill in the blank(s) with the appropriate word(s).