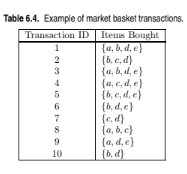
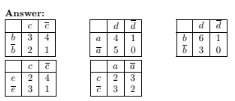
Draw a contingency table for each of the following rules using the trans- actions shown in Table 6.4.
.![]()
The original association rule mining formulation uses the support and confi-
dence measures to prune uninteresting rules
Computer Science & Information Technology
You might also like to view...
Every programmer must know all the details of what that programmer's team mates are doing in their projects to do the work assigned. Why?
What will be an ideal response?
Computer Science & Information Technology
After the following program is finished, how many bytes are written to the file t.dat?
``` import java.io.*; public class Test { public static void main(String[] args) throws IOException { DataOutputStream output = new DataOutputStream( new FileOutputStream("t.dat")); output.writeShort(1234); output.writeShort(5678); output.close(); } }``` a. 2 bytes. b. 4 bytes. c. 8 bytes. d. 16 bytes.
Computer Science & Information Technology