?In World History, ''td'' indicates the _________.
Fill in the blank(s) with the appropriate word(s).
table data tags
Computer Science & Information Technology
You might also like to view...
After disabling SSID broadcast, a network administrator still sees the wireless network listed in available networks on a client laptop. Which of the following attacks may be occurring?
A. Evil Twin B. ARP spoofing C. Disassociation flooding D. Rogue access point E. TKIP compromise
Computer Science & Information Technology
The m-estimate measure (with k = 2 and p+ = 0.58).
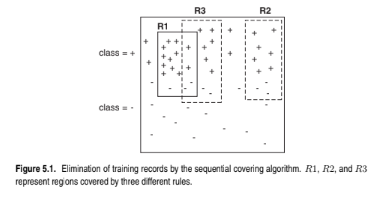
Figure 5.1 illustrates the coverage of the classification rules R1, R2, and R3.
Determine which is the best and worst rule according to:
Computer Science & Information Technology