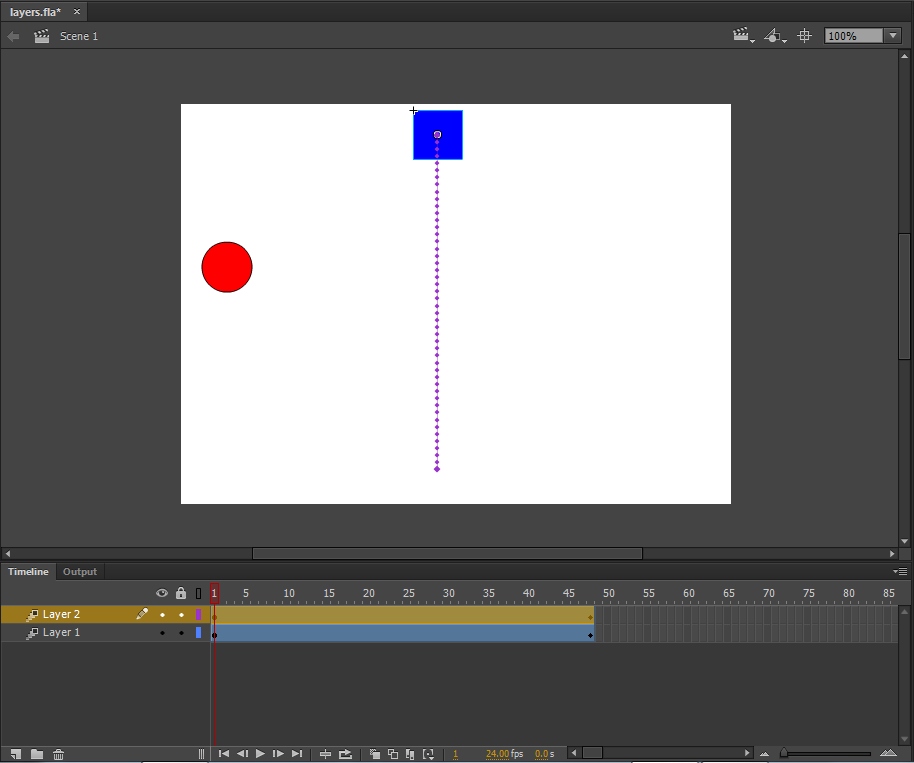
In the figure above, which layer is the active layer?
Fill in the blank(s) with the appropriate word(s).
Layer 2
Computer Science & Information Technology
You might also like to view...
A(n) ________ is a user-defined field that does not exist in the original dataset
Fill in the blank(s) with correct word
Computer Science & Information Technology
The security specialist role is also responsible for establishing and routinely evaluating the effectiveness of the vendor management program.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology