Provide the steps to Capture and Vview HTTP Traffic
In this part, you will use tcpdump to capture the content of HTTP traffic. You will use command
options to save the traffic to a packet capture (pcap) file. These records can then be analyzed using different applications that read pcap files, including Wireshark.
Step 1. Start the virtual machine and log in.
Start the CyberOps Workstation VM. Use the following user credentials:
Username: analyst
Password: cyberops
Step 2. Open a terminal and start tcpdump.
a. Open a terminal application and enter the command ifconfig.
[analyst@secOps ~]$ ifconfig
b. List the interfaces and their IP addresses displayed in the ifconfig output.
enp0s3 with 192.168.1.15 and lo with 127.0.0.1
c. While in the terminal application, enter the command sudo tcpdump –i enp0s3 –s 0
–w httpdump.pcap. Enter the password cyberops for the user analyst when prompted.
[analyst@secOps ~]$ sudo tcpdump –i enp0s3 –s 0 –w httpdump.pcap
[sudo] password for analyst:
tcpdump: listening on enp0s3, link-type EN10MB (Ethernet), capture size 262144
bytes
This command starts tcpdump and records network traffic on the enp0s3 interface.
The -i command option allows you to specify the interface. If not specified, the tcpdump
will capture all traffic on all interfaces.
The -s command option specifies the length of the snapshot for each packet. You
should limit snaplen to the smallest number that will capture the protocol information
in which you are interested. Setting snaplen to 0 sets it to the default of 262144, for
backwards compatibility with recent older versions of tcpdump.
The -w command option is used to write the result of the tcpdump command to a file.
Adding the extension .pcap ensures that operating systems and applications will be able
to read the file. All recorded traffic will be printed to the file httpdump.pcap in the
home directory of the user analyst.
Use the man pages for tcpdump to determine the usage of the -s and -w command
options.
d. Open a web browser from the launch bar within the Linux Workstation. Navigate to
www.altoromutual.com/bank/login.aspx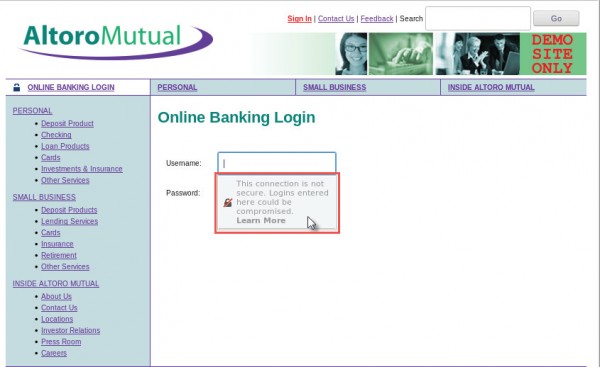
Because this website uses HTTP, the traffic is not encrypted. Click the Username field
to see the warning pop up.
e. Enter a username of Admin with a password of Admin and click Login.
f. Close the virtual web browser.
g. Return to the terminal window where tcpdump is running. Enter CTRL+C to stop the
packet capture.
Step 3. View the HTTP capture.
The tcpdump, executed in the previous step, printed the output to a file named httpdump.
pcap. This file is located in the home directory for the user analyst.
a. Click the File Manger icon on the desktop and browse to the home folder for the user
analyst. Double-click the httpdump.pcap file to open it in Wireshark.
b. In the Wireshark application, filter for http and click Apply.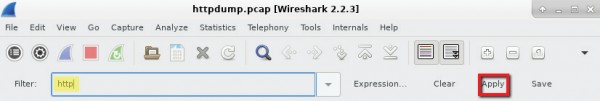
c. Browse through the different HTTP messages and select the POST message.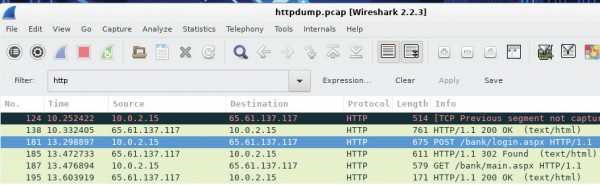
d. In the lower window, the message is displayed. Expand the HTML Form URL
Encoded: application/x-ww-form-urlencoded section.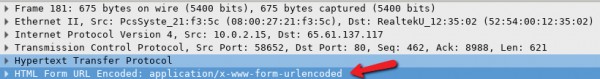
What two pieces of information are displayed?
The uid of Admin and passw of Admin
e. Close the Wireshark application.
You might also like to view...
Which Windows feature is an automatic grouping created to organize saved files?
A) Director B) Folder C) Library D) Compression
If a device is slow to provide input or output, the OS uses ____, which are areas of memory that hold data from one device before it is transferred to another device.?
A. ?windows B. ?swap files C. ?clouds D. ?buffers