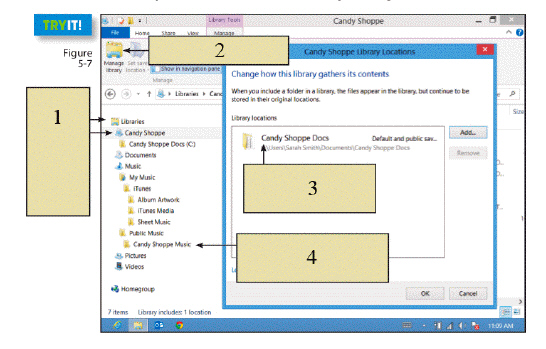
 In the figure above, item 2 is pointing to the ____.
In the figure above, item 2 is pointing to the ____.
A. custom library
B. Manage library icon
C. library folder
D. "real" location
Answer: B
Computer Science & Information Technology
You might also like to view...
Which of the following choices is the most accurate description of a countermeasure?
A. The company resource that could be lost due to an accident B. Any event with the potential to harm an information system through unauthorized access C. Controls put in place as a result of a risk analysis D. The annualized rate of occurrence multiplied by the single lost exposure
Computer Science & Information Technology
Pixels with a grayscale value of 0 are white.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology